The reason why you are in this site it’s because you are a computer geek or maybe just a curious one dreaming to be a hacker someday. Anyway, in this article, I am going to discuss to you the use of XSS Injection in order to know if a website you are currently using is vulnerable to attacks. Aside from that, this article also contain several tests for XSS Injection and its different types. So at the end of this article, you will be able to know that aside from manual XSS injection testing, there is an easy way to test XSS injection by using an add on tool in Mozilla Firefox. So what is XSS Injection?
XSS Injection stands for (Cross Site Scripting Injection)
It is the way of injecting malicious scripts into otherwise benign and trusted web sites.
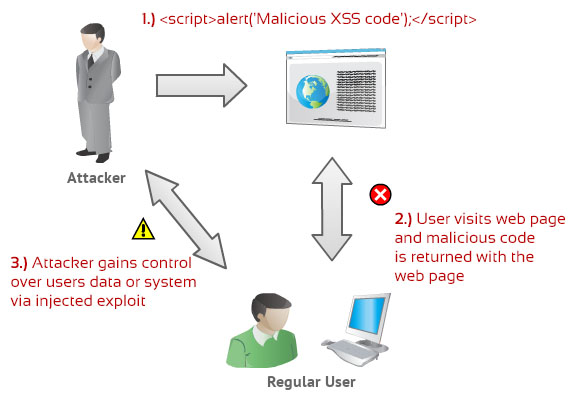
As you notice on the image below, 1) an attacker can use XSS to send a malicious script to an unsuspecting user. The end user’s browser has no way to know that the script should not be trusted, and will execute the script. Because it thinks the script came from a trusted source, after that, 2) User visits web page and malicious code is returned with the web page. For that reason, 3) the malicious script can access any cookies, session tokens, or other sensitive information retained by the browser and used with that site. So the attacker can gains control over users data or system via injected exploit.
There are 3 types of Cross Site Scripting Injection:
Reflected XSS Injection
Reflected attacks are those where the injected script is reflected off the web server, such as in an error message, search result, or any other response that includes some or all of the input sent to the server as part of the request. Reflected attacks are delivered to victims via another route, such as in an e-mail message, or on some other web site. When a user is tricked into clicking on a malicious link, submitting a specially crafted form, or even just browsing to a malicious site, the injected code travels to the vulnerable web site, which reflects the attack back to the user’s browser. The browser then executes the code because it came from a "trusted" server. Reflected XSS is also sometimes referred to as Non-Persistent or Type-II XSS.
Stored XSS Injection
Stored attacks are those where the injected script is permanently stored on the target servers, such as in a database, in a message forum, visitor log, comment field, etc. The victim then retrieves the malicious script from the server when it requests the stored information. Stored XSS is also sometimes referred to as Persistent or Type-I XSS.
DOM based XSS Injection
DOM Based XSS is a form of XSS where the entire tainted data flow from source to sink takes place in the browser, i.e., the source of the data is in the DOM, the sink is also in the DOM, and the data flow never leaves the browser. For example, the source (where malicious data is read) could be the URL of the page (e.g., document.location.href), or it could be an element of the HTML, and the sink is a sensitive method call that causes the execution of the malicious data (e.g., document.write)."
XSS Injection Diagram
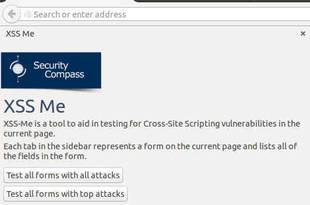
Since manual XSS Injection testing is time consuming, dont worry because there is an easy way to do it using an add on from mozilla firefox and that's it the XSS Me.
How to start with XSS Me?
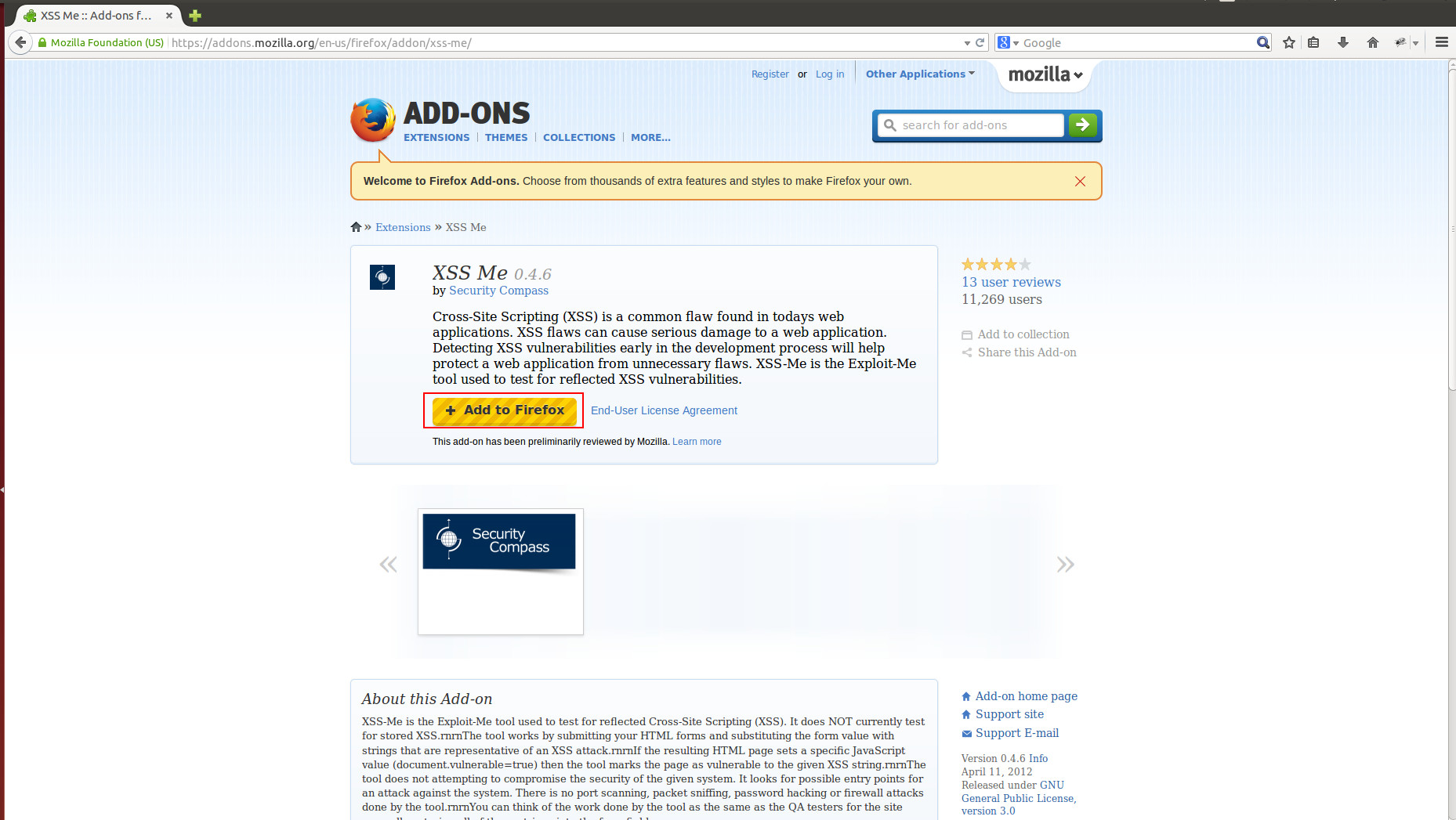
For you to start with XSS Me, Just go to your Mozilla Firefox browser and search the XSS Meaddon on google.
Once you are on the said site, Click the Add to Firefox button.
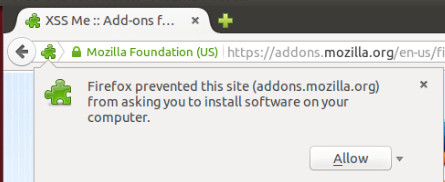 As you notice, Message will appear at the left top of the page asking to install software on your computer. Just click the Allow button.
As you notice, Message will appear at the left top of the page asking to install software on your computer. Just click the Allow button.
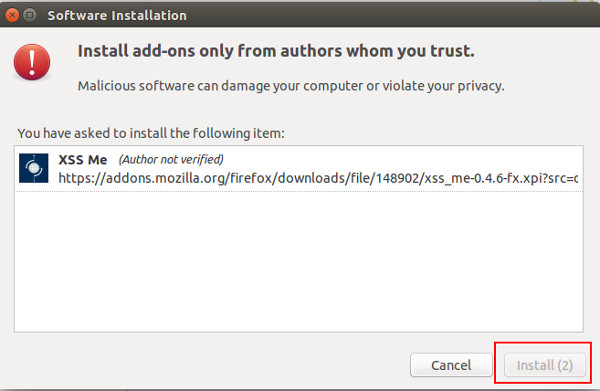
Click the Install button to install the XSS Me add on.
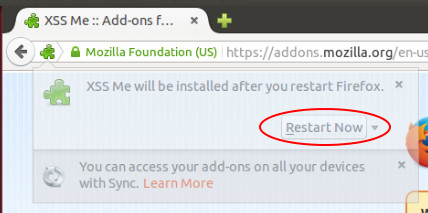 Once the installation was done, message at the top left part of the page will appear to Restart the browser. Click the Restart Now button.
Once the installation was done, message at the top left part of the page will appear to Restart the browser. Click the Restart Now button.
Once the browser was restarted, you can now proceed on testing the website. Just press Alt + T on your keyboard to appear the task bar of the Mozilla Firefox.
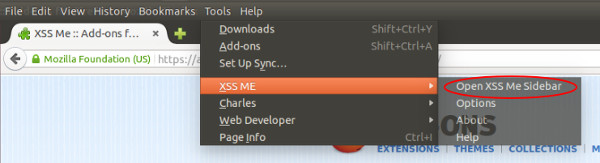 Click the Tools > XSS Me > Open XSS Me Sidebar
Click the Tools > XSS Me > Open XSS Me Sidebar
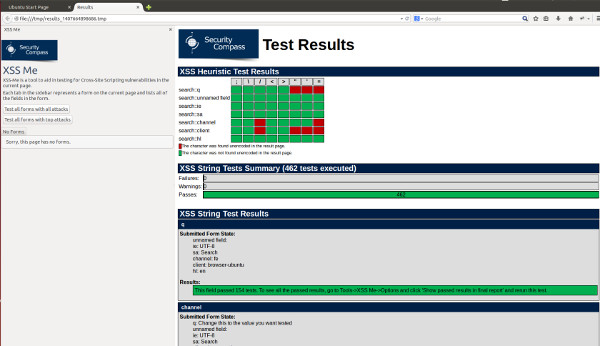
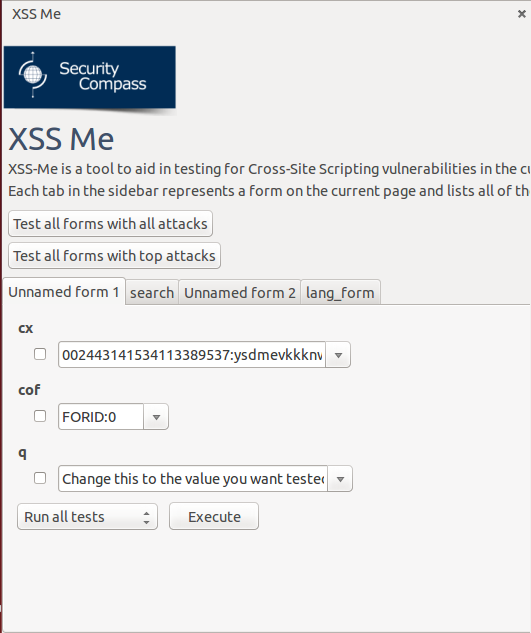 After that, XSS Me Sidebar will appear at the left part of the page. As you notice, It contains several input forms of the website you are currently in and the forms that you're going to inject scripts.
After that, XSS Me Sidebar will appear at the left part of the page. As you notice, It contains several input forms of the website you are currently in and the forms that you're going to inject scripts.
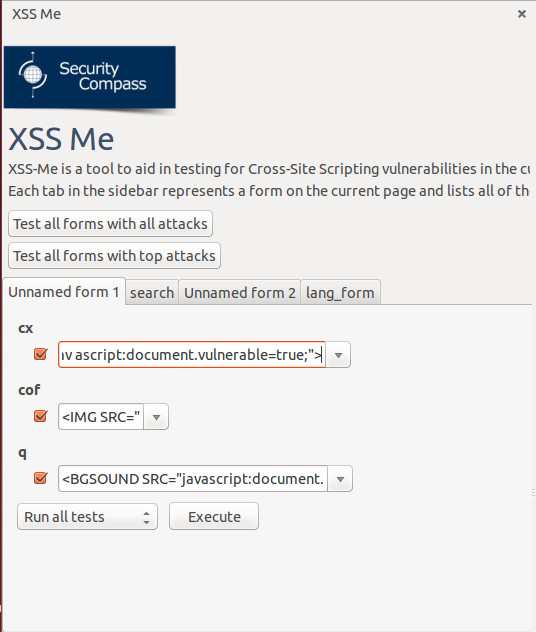 Select the available scripts on the dropdown lists that you prefer.
Select the available scripts on the dropdown lists that you prefer.
Before executing the test, check the checkbox beside the dropdown list. Once you are done, click the Execute button at the bottom part to execute the test.
The test scripts are currently running. Once all the scripts were done executing, a new tab will appear to display the results of the test if the website has XSS vulnerability.
And that's it. XSS Injection is now easy. A new tab will display the result of testing if the website you're testing is vulnerable to cross site scripting injection.